The SOC 2 certification process is considered to be painstaking, but it doesn’t need to be. We share our experience in this one-stop guide for other startups that are considering becoming SOC 2 Type II certified.
Every day, Analytics and Data Science teams across the globe trust Scribble Data to solve persistent business problems with data they can trust. Our Enrich platform processes and transforms a wide variety of raw data into ML-powered decision workflows that enable high-stakes decision-making. Being a data-centric business, we wanted to build a privacy-conscious architecture from day one. A robust, dependable, auditable engine is critical for generating and managing datasets safely and minimizing risk. We’ve always believed that we’re the custodians of trust when it comes to our customer’s data, and this is why we make every investment to establish and maintain the highest level of security and compliance. Achieving SOC 2 Type II certification showcases our ongoing commitment to privacy and security and reinforces our rigorous policies and procedures to safeguard customer data.
While we recently announced our SOC 2 Type II certification, we felt it would help other companies in a similar stage as well as domain as ours if we share our learnings and best practices to strike that balance between maintaining product development velocity as an early-stage startup and achieving a strong security posture.
What is SOC 2?
System and Organizational Controls (SOC 2), developed by the American Institute of Certified Public Accountants, is a voluntary compliance framework applicable to technology service providers or SaaS companies that handle or store customer data. In other words, SOC 2 defines the criteria that enable companies to maintain robust information security and protect customer data from unauthorized access and other vulnerabilities. The SOC framework is an objective, third party system that clearly indicates to your customers that they can trust your platform to handle their information in a secure way.
SOC 2 defines criteria for managing customer data based on five “trust service principles” — security, availability, processing integrity, confidentiality, and privacy.
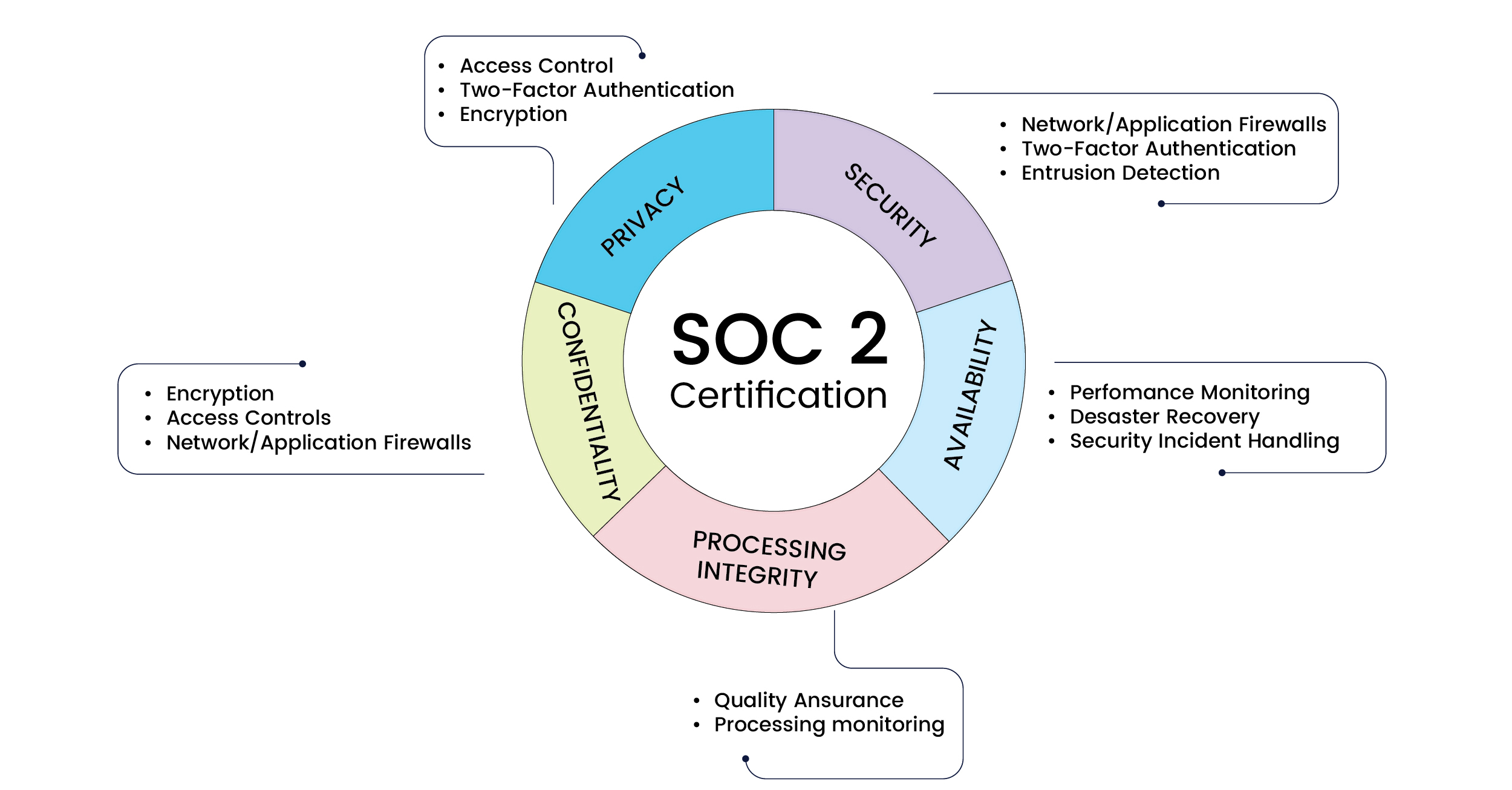
The key components of SOC 2
What are the different types of SOC2 audits and certifications?
SOC 2 audit reports exist in two forms: Type I and Type II. If you’re applying for a SOC 2 audit report for the first time, more often than not it’ll be Type I. In this type, the auditor reports on the company management’s description of the controls in operation and evaluates them at a single point in time. This is where they will also provide their feedback on the suitability of the design of those controls.
A Type II report isn’t vastly different from Type I, but it evaluates the controls over an extended period of time. The audit includes an additional section that evaluates the operating effectiveness of the controls that the company has put in place. The auditor tests operating effectiveness to validate that the controls are in place and functioning effectively as intended. The Type II report requires a higher level of rigor and is almost always required by enterprise customers.
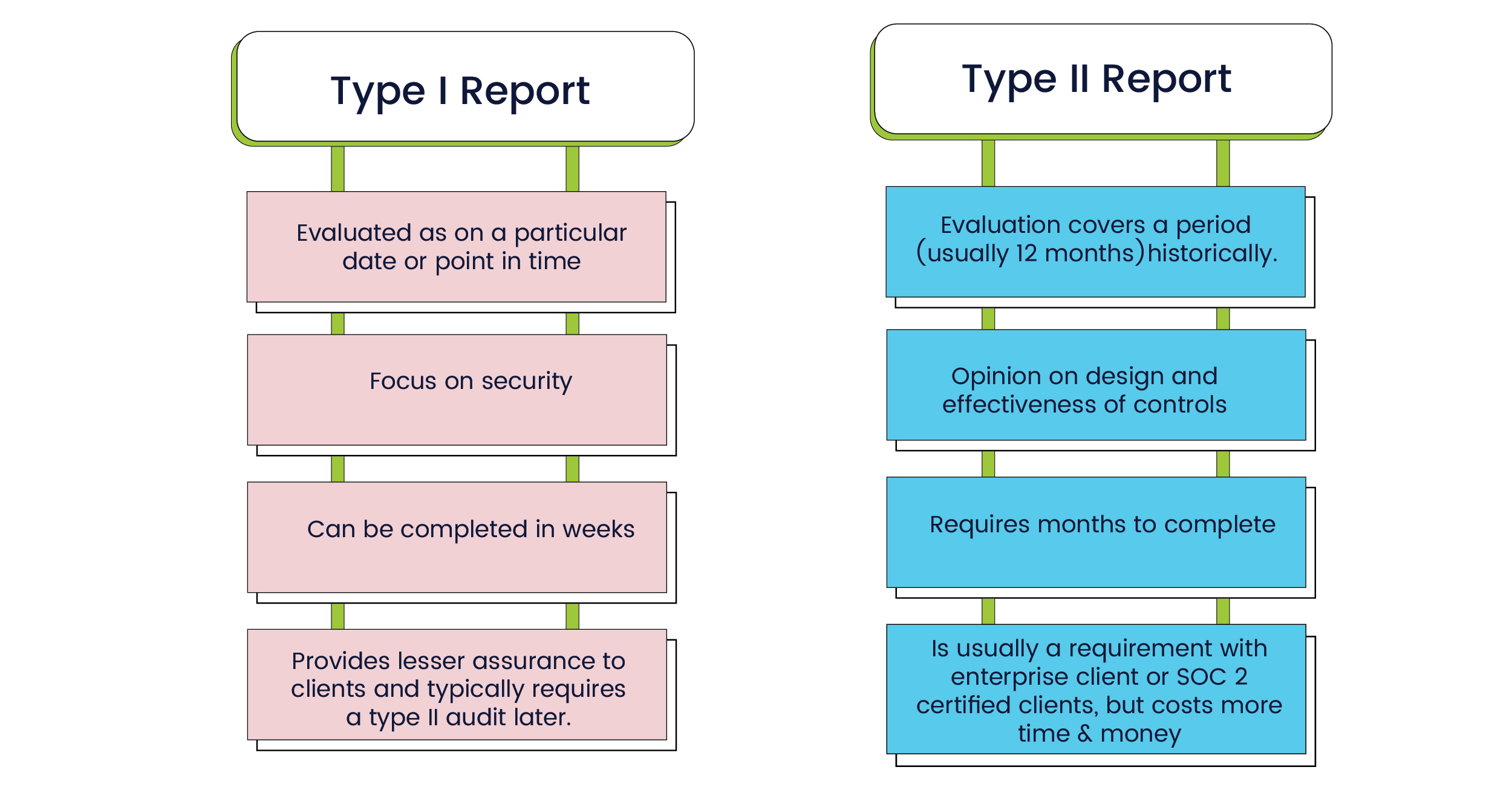
Differences between the SOC 2 Type I and SOC 2 Type II audit reports
How do I know if SOC2 is relevant to my business?
When you’re an early-stage startup, there are various opinions on whether or not you should invest in SOC 2. The usual opinion is that you can probably breathe easily if your business doesn’t handle sensitive customer business data. SOC 2 may be a lower priority for you since there might be fewer concerns around data security.
However, at Scribble Data, our focus was not so much on removing a friction point in deal cycles, but about building trust in our product. Data platforms must be built on a bedrock of trust, and our product is architected with security and trust as first-class considerations. Think code commit tagged pipelines, data anonymization, and GDPR record logging.
Key lessons learned along the way
SOC2 certification is a time-consuming, involved process and during the course of our audit, we had a bunch of learnings that we feel might be useful if you’re planning your SOC 2 journey.
Build a checklist of things you need to do
Getting certified requires a lot of preparation, across the organization. It’s not just a few individuals, but all the teams and employees involved in the successful evaluation of all your controls. Having a checklist helps, so we’ve listed out the important ones here
- Listing out all the requirements for certification – finding out the gaps that need to be addressed to make sure you’re prepared for your audit. These gaps could be around vetting privacy policies that come into play when we collect personal info from customers or around setting up a process for hiring or background checks.
- Setting up the appropriate processes to gather evidence for certification requirements
- Setting up controls, alerts, and follow-up mechanisms for recurring objectives. These recurring objectives could be the periodic follow-up for review of any data collected from customers or for review of the company policy around cybersecurity.
- Educating employees about the importance of being security minded – they need to understand why it’s important to be data-responsible and how it will help
Choose the right partner
While your company can always choose to DIY it, there are some obvious advantages to getting a partner when it comes to SOC 2 preparation. We especially recommend working with a partner for small to medium sized teams with bandwidth constraints. The experience and expertise they bring to the table can be very helpful and they ensure you’ve got all your bases covered.
There are many options for partners, and automation platforms available, so here are a few things to consider when you’re trying to decide on who you wish to work with:
- The partners and technology vendors you choose should have prior experience in working with organizations of your size and scale. If you’re a small business, do ask for client references that suggest they’ve had success with early scale clients that probably faced the kinds of challenges you will – employee bandwidth, technical debt, budget, and more.
- One of the reasons you’re looking for a partner is guidance and expertise. Always check if they’ll assign a dedicated case manager or account executive to handle your organization’s needs – you’ll have many questions, and sometimes complex security environments, it’s best to have access to a single point of contact (SPOC).
- Always ask your potential partner/auditor questions about their flexibility in working with startups and the responsiveness of their team. Don’t hesitate to call out anything in the delivery that doesn’t match with what is promised during the sales process.
- A compliance automation platform that walks you through the preparation processes step-by-step is always recommended. This platform should be more than just a knowledge base kind. It should be able to hook into your tech infrastructure (personnel, code repos, cloud providers) and pull status for reporting and alerting.
Automate your processes
Being SOC2 certified is a continuous process. Not a once-and-done thing. This means that processes need to be set up for the organization to continuously maintain its state of SOC2 compliance. Sure, you could consider using Excel sheets or Word documents to manage it, but it is unrealistic and not scalable at all. Utilizing a SOC 2 automation platform can greatly reduce the effort needed to achieve and maintain compliance.
A platform/tool that helps with maintaining a record of the current state of compliance, early warning on upcoming compliance issues, and alerting on critical compliance failures is invaluable for being SOC2 compliant in a painless manner. Being a 100% remote organization with a team (and customers) spread across the globe, having a global dashboard that showed an overview of the “state of compliance” was an essential feature.
If you’re evaluating an automation platform, here are a few factors you must ask yourself (and your vendor):
- Does this support integration with my core infrastructure?
- What pre-built SOC 2 draft policies does the platform come with that I can use as a starting point?
- Will this platform support my future needs as I apply for additional compliance standards, beyond SOC 2?
Make every employee aware of information security policies
Compliance and information security are not just the responsibility of a select few in the organization but in fact, something that everyone in the organization needs to be aware of, and responsible for. It’s essential to prepare all the functions in the company – from marketing to HR, sales, product management, tech, and more, for the compliance audit and to train them on data-responsible business practices.
The key milestones aren’t the same for everyone
Every organization is different, and the certification process as well as timelines depend on the type of organization, platform, or product being offered, the type of services being provided, as well as whether or not the organization has access to, and use of customer data (and to what level).
Therefore, It is important to scope out all the tasks necessary for the audit and certification while setting realistic milestones. There are a bunch of moving parts, and failure to do this can often result in the components of the audit slipping misalignment and delays, and a less than ideal SOC 2 reports. Clear and well-communicated timelines can help all the departments to plan ahead and prioritize their SOC 2 responsibilities. More importantly, it can help avoid last-minute changes in prioritization to meet deadlines.
Here’s a breakdown of the typical responsibilities of stakeholders across functions during the audit:
- Human Resources:
-
-
- Employee onboarding / offboarding processes
- Employee background checks
- Employee policy training
-
- Legal and Finance:
-
-
- Ensuring the right compliance policies are in place (e.g. NDA, contractor agreements, master service agreements, privacy policy, and more)
-
- Engineering and Product:
-
-
- Infrastructure changes necessary to ensure compliance
- Documenting penetration testing and risk assessments
- Demonstrating compliance with various security controls
-
- IT / Admin:
-
- Workstation security practices
- Managing employee account access
It’s always a good idea to assign a central information security officer who is responsible for ensuring compliance across all functions, and for building the company-specific compliance playbook. The engineering teams, especially in a data-first organization such as ours, need to be educated on the key role they play in the company’s security image since they have access to critical infrastructure as well as critical code, and usually have sensitive intellectual property on their official devices.
A few process changes that are necessary:
- Technical staff are to be provided infra/code access only on an as-needed basis
- Non-technical staff to be educated on how their roles will affect security at the organization
It’s best to start the employee training early. During onboarding, all employees should run through training sessions on best practices for security vis-a-vis their roles.
Why should you invest in SOC2 early?
In case you haven’t yet been asked for a SOC 2 certificate by a customer, chances are that you still have a bit of time and might be tempted to invest in other aspects of building your business first. However, we highly recommend investing in compliance sooner rather than later for two reasons:
- The earlier you invest, the easier it is to scale and maintain compliance
- Waiting too long to invest in the certification puts you at the risk of losing a late stage customer due to a lack of evidence that showcases the strength of your company’s security practices
While you can always create custom or “DIY” security policies, it’s always good to have an industry standard SOC2 report, as it significantly speeds up the deal closure/due diligence process at the customers’ end and also gives them confidence that you’re following industry best practices. If you’d like to know more about security practices at Scribble Data or would like to see a copy of our report, please feel free to write to us hello@scribbledata.io.



